Threats from phishing scams, malicious software, and compromised passwords are constantly increasing and pose an immediate risk to your privacy and the security of University data. Marshall University has implemented a new Multi-Factor Authentication (MFA) system that is required for all active account holders. When accessing a MFA-protected service, you will be prompted to enter your MUNet username and password and authenticate the login process with multi-factor authentication.
Instructions:
Before enrolling in Multi-Factor Authentication, you must first read the getting started instructions at the link below.
Multi-Factor Authentication setup instructions for your Marshall University account are available here:
Multi-Factor Authentication: Getting Started Instructions
The best and most convenient way to use Multi-Factor Authentication, is to download the Microsoft Authenticator app from either the App Store for iPhone or the Google Play Store for Android.
You will look for this icon on both platforms. To download, follow the link to your respective app store provided below:
What is it?
- MFA adds another layer of security to your online accounts
- Requires “two factor authentication” (2FA) to verify your identity when you log in to a service by:
- something you know (such as your password)
- something only you have (such as your mobile phone, on which you will receive a login confirmation notice via text or phone call)
Why should I do it?
- Provides enhanced protection of student and employee data caused by account credential compromise.
- Increasingly, hackers have targeted higher education institutions by using hacked credentials:
- to file taxes for employees
- to tamper with employee payroll deposits
- to attempt fraudulent access to student and employee’s bank accounts
- to harvest Social Security numbers for use in credit fraud
What are the benefits?
- Multi-factor authentication (MFA) is an effective way of stopping fraudulent account access by notifying you and requiring you to approve usage of your account
- MFA is essential to help safeguard access to critical systems
- MFA provides much stronger assurance that your information is only accessible to the intended people, and that MU’s systems and services remain available only to authorized account holders
Multi Factor Authentication FAQ
Multi-factor authentication should be used whenever possible because it immediately neutralizes the risks associated with compromised passwords by adding an additional layer of security to protect highly sensitive personal information. If a password is hacked, guessed, or phished, a bad actor would still need the required second factor on the account, making the stolen password alone useless.
Marshall has implemented many measures to prevent students and employees from falling victim to cyber hackers and those measures have helped the university successfully prevent serious cyber-attacks, spam email attacks and phishing email incidents. Increasingly, hackers are using sophisticated tools and mechanisms which, if unchecked, will continue to leave Marshall vulnerable to such attacks. Building on these security improvements, we have implemented measures to prevent credential theft. We have decided to implement MFA for all students and have chosen Microsoft Authenticator as our multifactor authentication system.
| Service: | Risk Factor: | Community: | Status/Availability Dates: |
|---|---|---|---|
| Microsoft 365 Services – student e-mail, OneDrive, Microsoft 365 ProPlus Apps, etc. | Reduce e-mail account abuse related to account takeovers by bad actors. | Students, alumni, faculty/staff using OneDrive | July 1st, 2019 |
| Campus ID Card TRANSACT Access | Protect financial information associated with TRANSACT stored value services | Students, faculty/staff using TRANSACT services. | April 3rd, 2019 |
| Outlook Web Access, Exchange Services | Reduce e-mail account takeovers and identity abuse. (e.g. impersonation of employees). | Faculty and staff | February 2019 for opt-in test group, late spring 2019 for wider campus rollout; required July 1, 2019. |
| Banner | Financial and student data security, audit compliance (e.g. mandatory password changes). | Employees with access to Banner Financial data; faculty with access to bulk student information (FERPA). | Introduced for pilot testing April 2019; required use July 1, 2019, IT Enterprise Apps team completed Banner 9 integration; requirement for exemption from 90-day password change on MUNet account. |
| Remote Access (VPN, muRemote, Remote Desktop Connections). | Ensure authorized access remote access to on-campus network (VPN), data (Banner and muBert), and server administration. | Students, faculty and staff who use Global Protect VPN; students, faculty and staff who use muRemote and RDP clients to access servers from off-campus. | Opt-in testing now; general availability April 2019; required July 1, 2019. |
| Web Portal Apps: Single-sign-on (SSO) | Ensure authorized access to student resources via myMU, muOnline, Library, etc. | All – opt-in/out options based on role (e.g. recruit, alumni and application support (e.g. some apps may not support MFA-based authentication). | TBA, currently testing in lab environment; options available for opt-out based on application or account holder role (e.g. recruiting, alumni portal, etc.). |
If you are off-campus, you should expect to receive an MFA verification prompt the first time you authenticate from either a new device or new location from which you have not previously verified using MFA.
If you are using an application which supports Office365 modern authentication, you will receive an option to ‘Approve sign-in request’ and ‘Don’t ask again for 60 days’. This option may be used on devices or locations you consider trusted, such as your mobile device or personal computer located at home. You should never use this option on public or shared-access computers.
- Push Notifications via Microsoft Authenticator App (Recommended for ease-of-use and security, requires cellular data or WiFi access)
- One-Time Security Codes via Microsoft Authenticator App (Use this method when your mobile device does not have access to cellular date or WiFi service)
- SMS (Text Message) (Recommended as an alternative verification method; SMS txt messages do require cellular or WiFi access)
- Phone Call
- OATH Hardware Token (available through Marshall IT service desk)
Note to MU Employees: Please see question “Can I use my Marshall University office phone as a verification method?” below.
- First, go to MFA Setup, where you will be asked to authenticate your Marshall email address. This will redirect you to the MU Single Sign-on Login page where you will login using your MUNet username and password.
- Choose “Notify me through app” to generate a customized QR code. This is used to associate your MUNet credentials with your mobile device. More detailed instructions are also provided at the Multi-Factor Authentication: Getting Started page.
- Using your mobile device, open the Microsoft Authenticator app and click the ‘+’ in the upper right-corner of the mobile app to add a new account.
- Next, the Microsoft Authenticator app will activate your device’s camera. Position the device to capture / ‘scan’ the provided QR code (see example here), then click the ‘Next’ button on the ‘Configure Mobile App’ webpage.
- You will receive a push notification on your phone to verify the Authenticator app is working correctly. Select the “Approve” button on the notification to verify.
Note to MU Employees: Please see section “Can I use my Marshall University office phone as a verification method?” below.
If you lost or already replaced your device, and your backup verification method is not available: Call or visit the IT Service Desk to have your MFA registration reset. Once reset, you can login to your Office365 account or go to MFA Setup and follow the prompts to set up your new device. Remember, it is recommended to set the Mobile App (Microsoft Authenticator app) with push notifications as your primary verification method.
If you are planning to get a new device, but still have access to your old device or backup verification method: You will need to set up a backup verification method that you can use when you receive your new device. To do so, login to MFA Setup which will prompt you for MFA verification…
- If you use the Microsoft Authenticator App: Under the “Authenticator app or Token” section, click “Delete” next to the “Authenticator app – [device name]” that is associated with your old device. Be sure to have “Authentication Phone” or “Alternate authentication phone” selected with a phone number you will still have access to when you dispose of your old device. This will serve as a backup method for logging in until you can get the Microsoft Authenticator app set up on your new device. Click “Save” when finished. Once you receive your new device, you can login to MFA Setup and follow the steps under the section “How do I configure the mobile app?” above.
- If you use SMS (text messages)/phone call verification, and do not plan on changing your phone number: No action needs to be taken. You will still receive SMS (text message) security codes on your new device when your carrier makes the switch. This is also the case if you use the Microsoft Authenticator app as your primary verification method, and already use SMS (text messages) as a backup method.
- If you use SMS (text messages)/phone call verification, and DO plan on changing your phone number: On the MFA Setup page, select either “Authentication phone” or “Alternate authentication phone” and enter a phone number you will have access to until you receive your new device. If you already know your new number, enter it in the “Authentication phone” section. Click “Save” when finished.
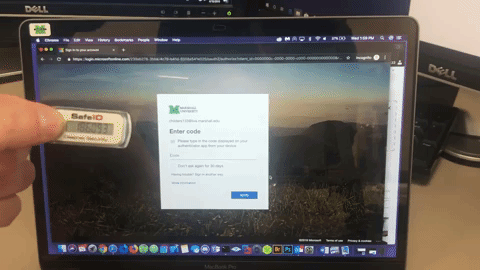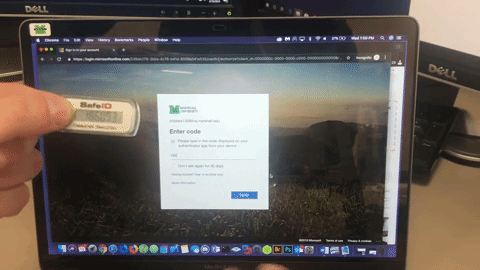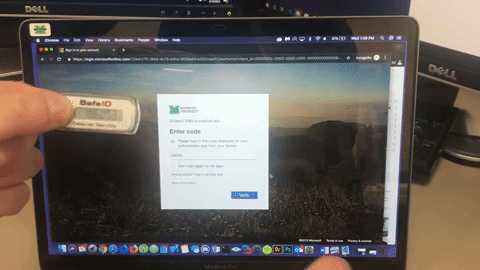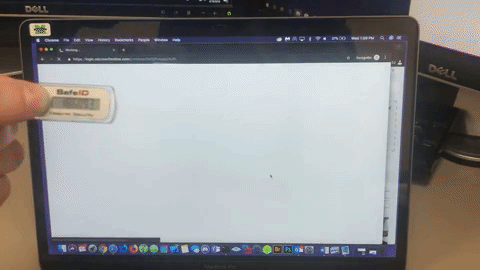
- First, go to MFA Setup
- Select “Disable” next to your Security Token
- Please return your OATH token to the IT Service Desk to avoid a $20 replacement fee.